Due to the increasing complexity of online activities, most hackers exploit known system vulnerabilities to write attack codes (Exploit Code) for infiltrating corporate information systems. Improper configuration settings or forgetting to update software patches in corporate host environments often lead to unauthorized access or other security risks in the information systems.
ACSI's professional cybersecurity teams, armed with extensive and practical experience, collaborates with internationally renowned vulnerability scanning tools. We assist and provide customers with vulnerability scanning services and result assessments, leveraging our expertise to identify system vulnerabilities and weaknesses early on. This proactive approach allows timely completion of vulnerability patching operations, preventing vulnerabilities from being exploited by hackers to launch attacks.
|
|
Description |
|
Assessment |
-
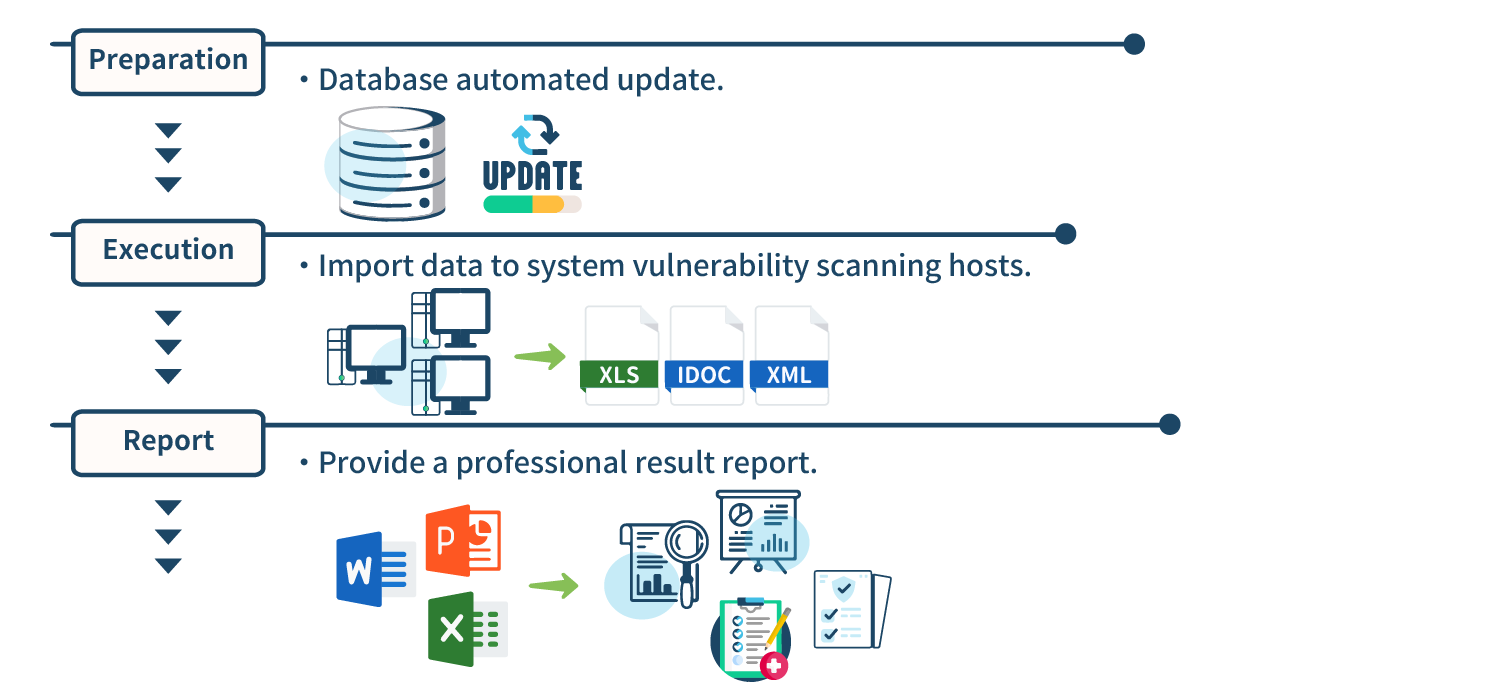
Execute detection for security issues related to host operating systems, network devices, and commonly used packaged software in the market (such as databases).
-
Updating of vulnerability databases
-
Web security checks, verifying the usage of SSL and exposure of SQL information.
|
|
Method |
-
Remote or on-site execution
-
Conducted using non-intrusive methods, excluding intrusion-type detection
|
|
Report |
-
English report, including:
-
Top 10 vulnerable hosts
-
Top 10 vulnerabilities and patching recommendations
-
Vulnerability ranking and vulnerability severity distribution
|