SAFE 3.0 Log Management
SAFE3.0 Introduction 2024_EN SUBTH
SAFE3.0 Introduction 2024_TH NOSUB
SAFE3.0 Introduction 2024_TH SUBTH
SAFE 3.0 helps enhance log management efficiency
SAFE 3.0 is a professional-level management system aiming at event log collection, preservation, analysis and auditing. It is a solution provider of event log management, a system with flexibility and scalability. In addition to providing supports on information security, network, host device logs, SAFE 3.0 is able to collect a variety of different log sources and formats. Through a user-defined log field format, SAFE 3.0 is able to provide an instant and valuable report to the management through its capabilities in massive data classification, analysis, and preservation.
SAFE 3.0 applies NoSQL database technology. It provides a keyword search function, as well as provides extensive reports that are compliant with the rules. It helps the analyzer to monitor event log in a timely manner to accelerate operational efficiency in processing historical event queries and production analysis reports. SAFE 3.0 can be deployed rapidly, supports all major brands of network security device logs, as well as reduces the time in need to introduce a new system. By making the minimum investment, corporation is able to establish a professional-level event log analysis and management platform. This can assist enterprises in achieving the objectives of log preservation and audit management.
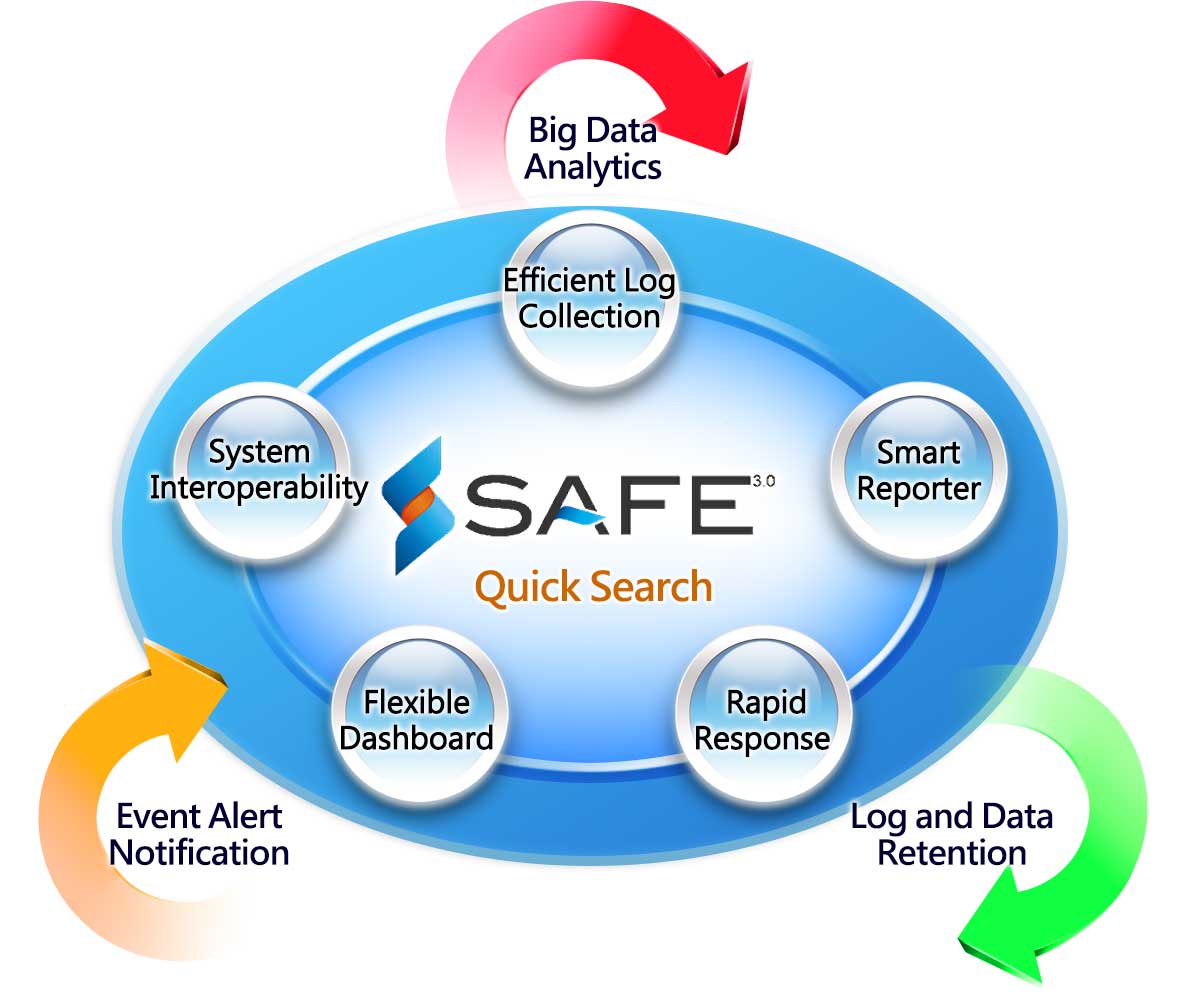
System Features
- NoSQL computing mechanism
With a rapid search engine, SAFE 3.0 has a high-quality performance made possible by a NoSQL system, and provides an outstanding user experience. - Apply high-efficiency keyword search function
In a pool of massive historic log, by typing in a keyword, the user can easily manage data mining tasks and retrieve results and production analysis charts rapidly. - Smart Reports
With more than 20 reports and a flexible smart report system built in, SAFE 3.0 can be customized by applying own-defined field formats and creates an ISO 27001 report with ease. Highly efficient report creating engine allows you to rapidly create those reports required by internal audit. - Rich and agile dashboard
More than 50 sorts of built-in patterns, SAFE 3.0 provides a real-time and comprehensive visible dashboard that is able to present messages in various combinations, which is helpful in getting key message on time, as well as getting to know the latest trends in terms of risk and safety. - In conjunction with practical application of personal data protection law
By using keyword search engine to look for suspicious event log, Safe 3.0 can assist enterprises in preventing a leakage of personal data. - Log integrity check
In compliance with NIST 800-92 log management standard, Safe 3.0 applies Secure Hash Algorithm (SHA-1) to ensure the integrity of log file and prevent data tampering. - A flexible external application system that connects and integrates data
Syslog can transfer the raw log to external application systems. The results can be exported and become a common text file, which can be read by external application systems. - Outstanding cross-platform log collection capability
Safe 3.0 is able to combine logs from heterogeneous platforms, and provides built-in and customized log analysis capabilities. This can meet the demands of diversifying log formats, and allow the system to move forward. - Supports all major brands of network security device logs
Support various log sources, including logs from information security, networks, servers, databases, and application systems. - Rapid installation procedures
Only three steps in need to complete installations. 1. Set up the source of log. 2. Set up the analysis rules on log field. 3. Set up the storage backup. Upon completion, the user can search logs by applying keyword search engine, and use the built-in default reports and dashboards to manage logs in accordance with real demands.
Customer Benefits
- Rapidly introduce a platform for massive log preservation and management. Reduce cost for system establishment.
- Assist enterprises in compliance with the personal data protection law. Meet the management needs for log audit. Reduce operational risk.
- Establish a centralized log management platform. Reduce management costs. Achieve high return of investment (ROI) by making a minimum amount of investment.
SAFE 3.0 Hardware Requirement
- CPU: 4 Cores or above
- Memory: 32GB or above
- Disk: SATA 2.5TB or better
- Network: 1Gbps
- OS Support: Linux (Ubuntu)
SAFE 3.0 Appliance
Product Specifications
- SAFE 3.0 Software log processing capabilities: Supports receiving more than 1,000 event log per second(EPS). Supports more than 200 source devices.
- Support firewall. Collect IDS / IPS and anti-virus software log data. Support host system resource monitoring and measurement log collection.
- Provide key word search function. Allow for data searching by the fields of log source, time and IP address.
- Safe 3.0 has alert notifications.
- Support standard Syslog message mode to retrieve logs.
- Once being saved, Safe 3.0 switches into read-only mode to avoid log tampering.
- Provide log preservation and compression function. Allow for storing 10TB (or more) log data after being compressed.
- Provide Web interface configuration and management, with Web management interface.
- Provide log backup function to prevent data loss from a single disk disorder.
- Capable of providing customized reports and support html or PDF report format.
- Provide network abnormal event analysis and TOP N ranking reports. Allow for customized reports, real-time production reports, or delivering reports on a regular basis.
- Provide customized dashboards that allow for specifying the time zone. Generate real-time data analysis charts on Web interface.
- Support IPv6, in conjunction with international IPv6 Ready Logo.
- Capabilities of preventing log tampering (Write Once Read Many).Once being saved, Safe 3.0 switches into read-only mode to avoid log tampering.
- Apply Secure Hash Algorithm (SHA-1) to ensure the integrity of log file during transmission, as well as ensure that received log have not been tampering or being replaced.
